
Index

DATA AUTHENTICITY
Proving that files and records have been made on a certain date and have not been tempered with afterwards is very important for a legally trusted ELN. The issue of data integrity is particularly important for electronic records, as it is inherently easy to edit digital documents without a trace.
This ELN allows to prove that all records are authentic and were made on a certain date. This ELN allows to eliminate issues of personnel integrity. Project supervisors can use their automatically issued digital keys (digital signatures) to verify any ELN records.
Digital signatures
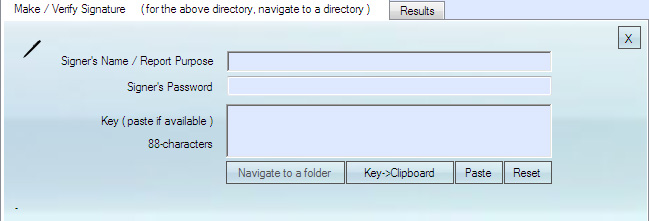
This block of the program allows to prove the data in a folder or in a project existed at a specific point in time.
It operates by comparing two keys:
Key 1 = current key for a directory
Key 2 = pre-issued key, provided on demand by a trusted third party that time-stamped the key upon receipt
(it is possible to do free discoverable time stamping by E-mail - see below)
Examples of the Digital Signatures module in use.
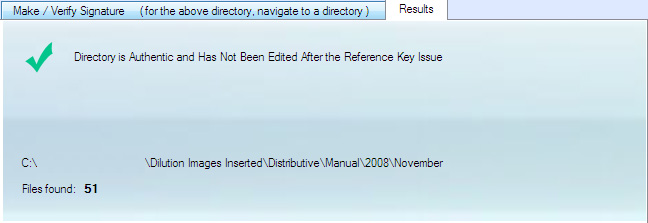
Example 1: Successful audit. Automatically generated key matches the backed up audited data.
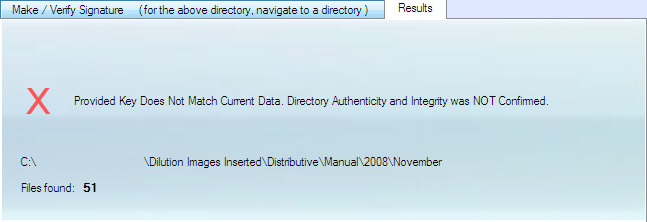
Example 2: Failed audit. Automatically generated key does not match the backed up audited data
because one of the sentences in the stored files was altered in a text editor.
Pre-issued key is generated either manually, via digital signature module, or automatically by Audit module.
It is important to generate this reference key such that the date of its creation could be legally proven later.
In addition to commercial vendors that do exacly that and store the key as a paid service, a good option is to send the key by email, even to key creator's own email account on an independent email server (for exmaple, gmail.com). Legal email discovery can be used to prove that this key was indeed emailed on the claimed date.
During ELN audit, Key 2 is recovered from any of the trusted locations and verified across the ELN data using the digital signatures module in the ELN tab. The digital signatures algorithm detects every modification in the data, such as an extra space character in one of the ELN pages or a single byte altered in any document or a file within the keyed directory.
The key is generated using SHA512 function found in many industry-standard security applications and protocols.
AUTOMATIC AUDIT, REPORTING AND BACKUP
BiochemLabSolutions ELN can generate project reports and send reference keys automatically by email.